Agile approach for
threat detection & protection


Overview
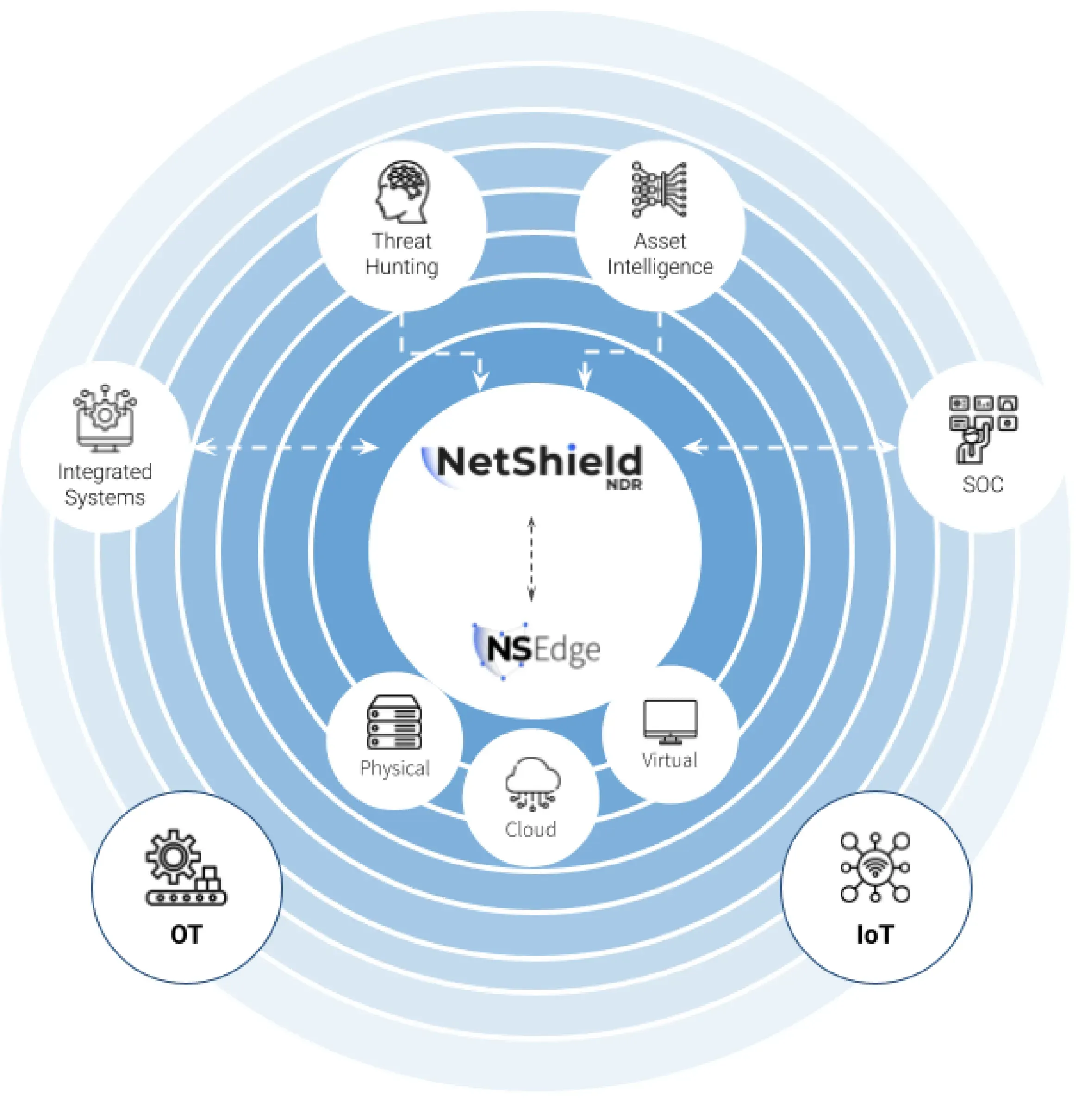
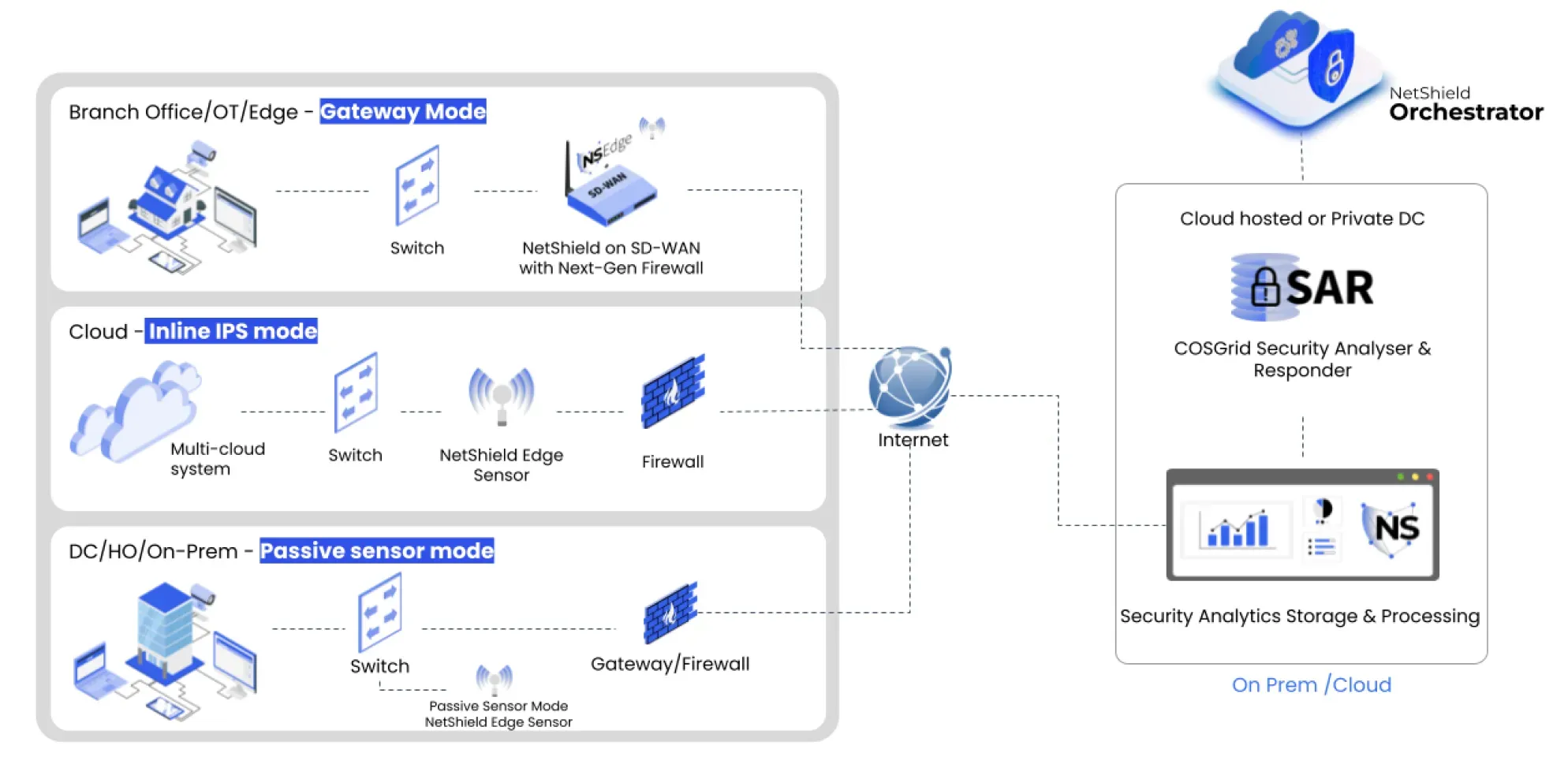
NetShield NDR is COSGrid's AI-powered Network Detection and Response platform that identifies and contains post-breach threats within network environments. Leveraging advanced machine learning, it monitors real-time traffic flows, detects sophisticated attacks including ransomware and insider threats, and provides automated response capabilities to strengthen organizational cyber resilience.
Challenges
Limited Network Visibility Across Modern Infrastructure
- Hybrid cloud and remote work blind spots
- Unmonitored internal traffic and lateral movement
- Unmanaged IoT and OT device vulnerabilities

Inefficient Threat Detection and Response Operations
- Extended threat dwell time and delayed detection
- Alert overload and false positive fatigue
- Resource-intensive manual investigation processes
Complex Multi-Vendor Security Architecture
- Fragmented security tool management overhead
- Specialized skills requirements and resource gaps
- Encrypted traffic analysis and visibility limitations

Business Risk and Operational Impact
- Security incident operational disruption costs
- Regulatory compliance and audit complexities
- Escalating cybersecurity investment requirements
Core Features
4D Traffic Analysis & Visualization
 Real-time traffic analysis and monitoring
Real-time traffic analysis and monitoring  Automated device discovery and classification
Automated device discovery and classification  Multi-dimensional network traffic visualization
Multi-dimensional network traffic visualization

Unified Security Platform Integration
 Consolidated multi-technology security architecture
Consolidated multi-technology security architecture  Seamless orchestration and third-party integrations
Seamless orchestration and third-party integrations  Edge intelligence for rapid remediation
Edge intelligence for rapid remediation

AI-Powered Threat Detection & Response
 Machine learning behavioral anomaly detection
Machine learning behavioral anomaly detection  Encrypted traffic analytics and fingerprinting
Encrypted traffic analytics and fingerprinting  Proactive threat hunting with intelligence
Proactive threat hunting with intelligence
Network Segmentation & Access Control
 Micro-segment and zero trust access
Micro-segment and zero trust access  Encrypted tunnels for channel protection
Encrypted tunnels for channel protection  East-west traffic monitoring capabilities
East-west traffic monitoring capabilities
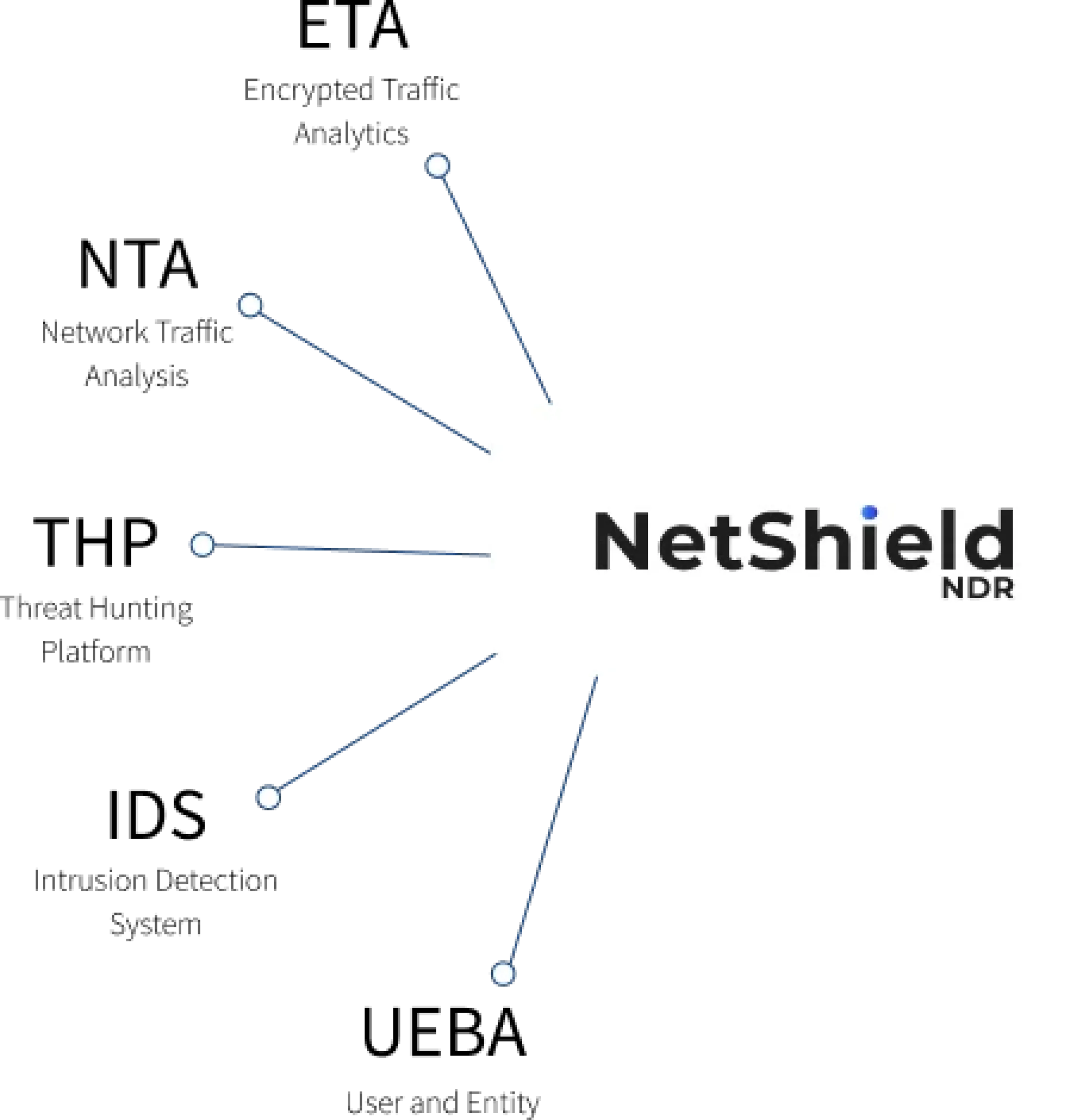
What Sets NetShield NDR Apart From The Rest?

Encrypted Traffic Analytics with SPLT Intelligence
 TLS/SSH fingerprinting without decryption capabilities
TLS/SSH fingerprinting without decryption capabilities  Sequence packet length timing behavioral analysis
Sequence packet length timing behavioral analysis  Initial data packet metadata threat detection
Initial data packet metadata threat detection

4D Traffic Analysis and Visualization Platform
 Multi-dimensional traffic metadata capture and correlation
Multi-dimensional traffic metadata capture and correlation  Auto-discovery and classification of network assets
Auto-discovery and classification of network assets  Interactive visual dashboards with contextual intelligence
Interactive visual dashboards with contextual intelligence
Distributed Edge Intelligence with Cloud Orchestration
 NetShield Edge real-time processing at perimeter
NetShield Edge real-time processing at perimeter  Cloud-based SAR centralized correlation and analytics
Cloud-based SAR centralized correlation and analytics  Synchronized metadata streaming for rapid response
Synchronized metadata streaming for rapid response

IoT/OT Security with ML-Powered Anomaly Detection
 Specialized IoT device behavioral baseline creation
Specialized IoT device behavioral baseline creation  Machine learning statistical anomaly detection algorithms
Machine learning statistical anomaly detection algorithms  Real-time OT protocol monitoring capabilities
Real-time OT protocol monitoring capabilities
Use Cases

Threat Detection & Response
 Detect unknown attacks using behavioral baselining.
Detect unknown attacks using behavioral baselining.  Automate containment workflows for rapid mitigation.
Automate containment workflows for rapid mitigation.

Lateral Movement Prevention
 Identify unusual internal traffic patterns quickly.
Identify unusual internal traffic patterns quickly.  Block compromised hosts from internal networks.
Block compromised hosts from internal networks.

IoT & OT Security Monitoring
 Monitor IoT devices for anomalous communications.
Monitor IoT devices for anomalous communications.  Alert on unauthorized OT protocol activities.
Alert on unauthorized OT protocol activities.

Encrypted Traffic Analysis
 Fingerprint TLS/SSH flows without decryption.
Fingerprint TLS/SSH flows without decryption.  Surface hidden threats within encrypted streams.
Surface hidden threats within encrypted streams.

Forensic Investigation
 Correlate historical events across network metadata.
Correlate historical events across network metadata.  Generate audit-ready incident timelines automatically.
Generate audit-ready incident timelines automatically.

Compliance & Audit Support
 Provide evidence for regulatory reporting needs.
Provide evidence for regulatory reporting needs.  Maintain continuous logs for audit readiness.
Maintain continuous logs for audit readiness.
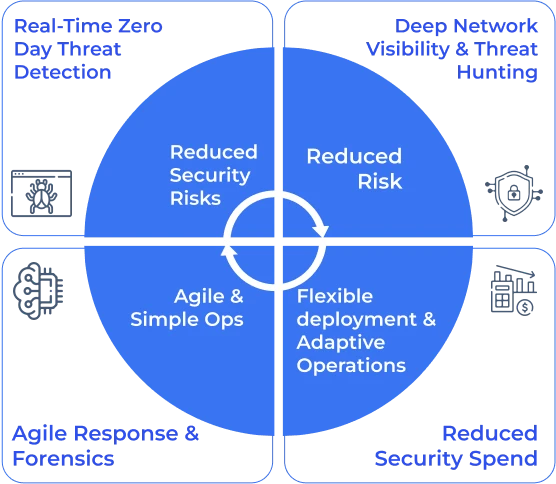
Benefits of NetShield NDR
That helps your organisation worry less about network security
3X higher accuracy in detection through multi-pronged approach
Industry leading TAT with response time within 30 secs to 1 hour – Local & Edge intelligence
Protection with multiple levels of SLAs & criticality - both Adaptive and policy based for optimal analysis
Ease and effective management through Centralized vs Distributed vs Hybrid anomaly detection
Superior TCO converged product - probes collection to threat detection to threat remediation